|
大版主
- 帖子:9006
- 注册:
2006-05-23
- 来自:长江嘉陵江接合部
|
发表于:
2006-12-10 20:27
|
短消息
资料
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RsRavMon]
"Type"=dword:00000010
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):22,00,45,00,3a,00,5c,00,52,00,69,00,73,00,69,00,6e,00,67,00,\
5c,00,52,00,61,00,76,00,5c,00,52,00,61,00,76,00,6d,00,6f,00,6e,00,64,00,2e,\
00,65,00,78,00,65,00,22,00,00,00
"DisplayName"="RsRavMon Service"
"Group"="TDI"
"DependOnService"=hex(7):52,00,73,00,43,00,43,00,65,00,6e,00,74,00,65,00,72,00,\
00,00,00,00
"DependOnGroup"=hex(7):00,00
"ObjectName"="LocalSystem"
"FailureActions"=hex:00,00,00,00,00,00,00,00,00,00,00,00,03,00,00,00,52,00,61,\
00,01,00,00,00,60,ea,00,00,01,00,00,00,60,ea,00,00,01,00,00,00,60,ea,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RsRavMon\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,00,01,00,00,\
00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,00,01,01,00,00,00,00,00,\
05,12,00,00,00,00,00,18,00,ff,01,0f,00,01,02,00,00,00,00,00,05,20,00,00,00,\
20,02,00,00,00,00,14,00,8d,01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,\
00,18,00,fd,01,02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,\
00,00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RsRavMon\Enum]
"0"="Root\\LEGACY_RSRAVMON\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001
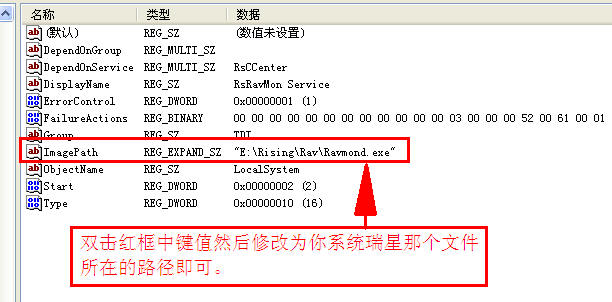
将上面的红色字符保存为后缀名为“reg”的文件名,再将它导入注册表,然后再进入注册表里找到[HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\RsRavMon]这路径中的“RsRavMon”这个键值名下右面的参见下图片
 附件: 附件:
下载次数:223
文件类型:image/pjpeg
文件大小:
上传时间:2006-12-10 20:27:28
描述:
预览信息: EXIF信息- User Comment : LEAD Technologies Inc. V1.01
|