networkedition - 2010-3-29 14:32:00
Log is generated by FreShow.
[wide]http://cn.xm12.host.35.com/
[script]http://cssc.3d-game.com/css.js?width=700&height=600&keyword=ua556
[frame]http://186.319today.info:1000/360/index.html?id=1001
[object]http://186.319today.info:1000/360/mp-.html?id=1001
[object]http://186.319today.info:1000/360/1001/a.jpg
[object]http://my.me-1.info:8886/Down/my/1001.exe
[script]http://186.319today.info:1000/360/\'mp/c.jpg\'
[script]http://186.319today.info:1000/360/\'mp/d.css\'
[script]http://186.319today.info:1000/360/\'mp/e.jpg\'
[script]http://186.319today.info:1000/360/\'mp/f.css\'
[frame]http://count25.51yes.com/sa.aspx?id=259340713&refe='+window.parent.location+'&location=http%3A//'+paramsArr[0]+'&color=32x&resolution=1280x1024&returning=1&language=zh-cn&ua=Mozilla/4.0%20%28compatible%3B%20MSIE%206.0%3B%20Windows%20NT%205.1%3B%20SV1%3B%20.NET%20CLR%202.0.50727%3B%20.NET%20CLR%203.0.04506.30%29
用户系统信息:Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729; InfoPath.2)
青松1 - 2010-3-29 15:37:00
请教
为什么我用FreShow1.5解不出版主那样的代码
只能解出下面的
Log is generated by FreShow.
[wide]http://cn.xm12.host.35.com
[script]http://cssc.3d-game.com/css.js?width=700&height=600&keyword=ua556
[frame]http://186.319today.info:1000/360/index.html?id=1001
[script]http://186.319today.info:1000/360/\'check.php?id="
[script]http://186.319today.info:1000/360/\'safe.js\'
[frame]http://186.319today.info:1000/360/about:blank
[frame]http://186.319today.info:1000/360/about:blank
[frame]http://186.319today.info:1000/360/about:blank
[script]http://186.319today.info:1000/360/\"http://js.tongji.linezing.com/1389409/tongji.js\"
[script]http://186.319today.info:1000/360/\"http://js.tongji.linezing.com/1407368/tongji.js\"
[script]http://186.319today.info:1000/360/\"http://js.tongji.linezing.com/"+tongji_num+"/tongji.js\"
[frame]http://count25.51yes.com/sa.aspx?id=259340713&refe='+window.parent.location+'&location=http%3A//'+paramsArr
[0]+'&color=32x&resolution=1280x1024&returning=1&language=zh-cn&ua=Mozilla/4.0%20%28compatible%3B%20MSIE%206.0%3B%20Windows%
20NT%205.1%3B%20SV1%3B%20.NET%20CLR%202.0.50727%3B%20.NET%20CLR%203.0.04506.30%29
networkedition - 2010-3-29 15:52:00
这个要分析代码,地址很隐蔽,看懂代码就知道咋解密了。
networkedition - 2010-3-29 16:25:00
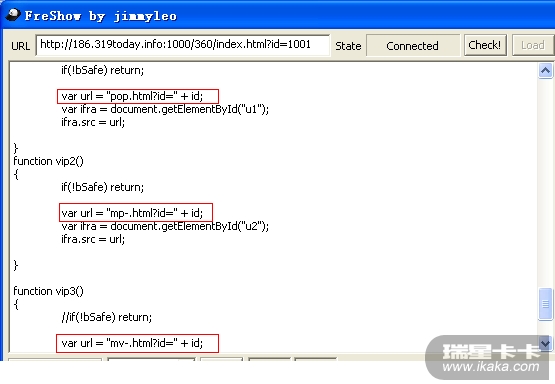
源代码太长了,就将关键的地方截屏,见下图,至于id的值嘛,因解密的这个链接地址id=1001,那么简单的说id取值就是1001,id也可等于其它的值(详见取id值部分代码),解密出来的网马文件大小都是一样的,md5值应该也一样, 都是同一个文件,只不过文件名不一样罢了。你可以试试,将id换成其它的值,也能获取到源代码的,对比一下就知道了。

zzzkkkmmm - 2010-3-29 19:59:00
关于:hxxp://cn.xm12.host.35.com/解密的日志(全体输出 - 8):
Level 0>http://cn.xm12.host.35.com/
Level 1>http://cn.xm12.host.35.com/index.swf
Level 1>http://001.wtt365.com:8080/wtt/mainscript.jsp?companyid=122067&color=04&side=1&showflag=45&op=&gid=&c=1&ws=&ic=&closegroup=&location=+href+
Level 1>http://cssc.3d-game.com/css.js?width=700&height=600&keyword=ua556
Level 2>http://count25.51yes.com/sa.aspx?id=259340713&refe=+window.parent.location+&location=http%3a//+paramsarr
Level 2>http://186.319today.info:1000/360/index.html?id=1001
Level 3>http://my.me-1.info:8886/down/my/1001.exe+ytavp
Level 3>http://my.me-1.info:8886/down/my/1001.exe
日志由 Redoce2.0第45次修正版于 2010-3-29 19:56:52 生成。
落尘化 - 2010-3-30 11:28:00
:kaka9: 我想知道查出这些个病毒网址后,如何防止它再次注入。
我的网址也被注入了。
落尘化 - 2010-3-30 11:29:00
我也查出了这个网马。太可恶了
http://186.319today.info:1000/360/index.html?id=1001
© 2000 - 2026 Rising Corp. Ltd.
