|
大版主
- 帖子:72578
- 注册:
2003-04-10
- 来自:
|
发表于:
2006-08-09 23:13
|
只看楼主
短消息
资料
关于杀掉Trojan.PSW.QQPass类木马瑞星监控不能打开问题
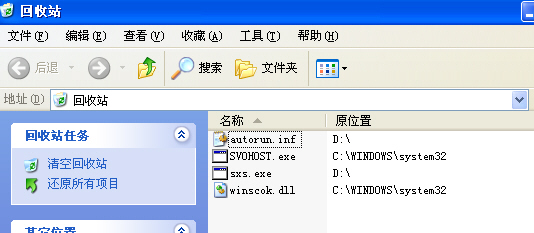
Trojan.PSW.QQPass是瑞星“橙色八月”专杀工具中提到的一类木马。今天拿到一个样本Trojan.PSW.QQPass.pqg。植入系统,试了一下“橙色八月专用工具”。 本来,试验的目的是想看看这个专用工具能否解决杀毒后瑞星监控不能加载问题;但是试验结果令人沮丧。这只木马,瑞星18.39.22可杀,但用“橙色八月专用工具”在安全模式下却杀不到! 于是我在备份的注册表中找到瑞星相关注册表项的正常值,做成一个.reg文件。手工杀毒后(木马文件见附图),将这个Rising.reg导入注册表。重启系统后观察。结果——瑞星的各项监控均可正常加载。 Rising.reg内容如下:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"RavTask"="\"C:\\Program Files\\Rising\\Rav\\RavTask.exe\" -system"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ExpScaner]
"Type"=dword:00000001
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):5c,3f,3f,5c,43,3a,5c,50,72,6f,67,72,61,6d,20,46,69,6c,65,73,5c,\
52,69,73,69,6e,67,5c,52,61,76,5c,45,78,70,53,63,61,6e,2e,73,79,\
73,00
"DisplayName"="ExpScaner"
"Group"="TDI"
"DependOnService"=hex(7):42,61,73,65,54,44,49,00,00
"DependOnGroup"=hex(7):00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ExpScaner\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,\
00,01,00,00,00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,\
00,01,01,00,00,00,00,00,05,12,00,00,00,00,00,18,00,ff,01,0f,00,\
01,02,00,00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,14,00,8d,\
01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,00,18,00,fd,01,\
02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,00,\
00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ExpScaner\Enum]
"0"="Root\\LEGACY_EXPSCANER\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookCont]
"Type"=dword:00000001
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):5c,3f,3f,5c,43,3a,5c,50,72,6f,67,72,61,6d,20,46,69,6c,65,73,5c,\
52,69,73,69,6e,67,5c,52,61,76,5c,48,4f,4f,4b,43,4f,4e,54,2e,73,\
79,73,00
"DisplayName"="HookCont"
"Group"="TDI"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookCont\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,\
00,01,00,00,00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,\
00,01,01,00,00,00,00,00,05,12,00,00,00,00,00,18,00,ff,01,0f,00,\
01,02,00,00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,14,00,8d,\
01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,00,18,00,fd,01,\
02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,00,\
00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookCont\Enum]
"0"="Root\\LEGACY_HOOKCONT\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookReg]
"Type"=dword:00000001
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):5c,3f,3f,5c,43,3a,5c,50,72,6f,67,72,61,6d,20,46,69,6c,65,73,5c,\
52,69,73,69,6e,67,5c,52,61,76,5c,48,6f,6f,6b,52,65,67,2e,73,79,\
73,00
"DisplayName"="HookReg"
"Group"="TDI"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookReg\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,\
00,01,00,00,00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,\
00,01,01,00,00,00,00,00,05,12,00,00,00,00,00,18,00,ff,01,0f,00,\
01,02,00,00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,14,00,8d,\
01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,00,18,00,fd,01,\
02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,00,\
00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookReg\Enum]
"0"="Root\\LEGACY_HOOKREG\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookSys]
"Type"=dword:00000001
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):5c,3f,3f,5c,43,3a,5c,50,72,6f,67,72,61,6d,20,46,69,6c,65,73,5c,\
52,69,73,69,6e,67,5c,52,61,76,5c,48,6f,6f,6b,53,79,73,2e,73,79,\
73,00
"DisplayName"="HookSys"
"Group"="TDI"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookSys\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,\
00,01,00,00,00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,\
00,01,01,00,00,00,00,00,05,12,00,00,00,00,00,18,00,ff,01,0f,00,\
01,02,00,00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,14,00,8d,\
01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,00,18,00,fd,01,\
02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,00,\
00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HookSys\Enum]
"0"="Root\\LEGACY_HOOKSYS\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RsCCenter]
"Type"=dword:00000010
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):22,43,3a,5c,50,72,6f,67,72,61,6d,20,46,69,6c,65,73,5c,52,69,73,\
69,6e,67,5c,52,61,76,5c,43,43,65,6e,74,65,72,2e,65,78,65,22,00
"DisplayName"="Rising Process Communication Center"
"Group"="COM Infrastructure"
"DependOnService"=hex(7):52,70,63,53,73,00,00
"DependOnGroup"=hex(7):00
"ObjectName"="LocalSystem"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RsCCenter\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,\
00,01,00,00,00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,\
00,01,01,00,00,00,00,00,05,12,00,00,00,00,00,18,00,ff,01,0f,00,\
01,02,00,00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,14,00,8d,\
01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,00,18,00,fd,01,\
02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,00,\
00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RsCCenter\Enum]
"0"="Root\\LEGACY_RSCCENTER\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RsRavMon]
"Type"=dword:00000010
"Start"=dword:00000002
"ErrorControl"=dword:00000001
"ImagePath"=hex(2):22,43,3a,5c,50,72,6f,67,72,61,6d,20,46,69,6c,65,73,5c,52,69,73,\
69,6e,67,5c,52,61,76,5c,52,61,76,6d,6f,6e,64,2e,65,78,65,22,00
"DisplayName"="RsRavMon Service"
"Group"="TDI"
"DependOnService"=hex(7):52,73,43,43,65,6e,74,65,72,00,00
"DependOnGroup"=hex(7):00
"ObjectName"="LocalSystem"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RsRavMon\Security]
"Security"=hex:01,00,14,80,90,00,00,00,9c,00,00,00,14,00,00,00,30,00,00,00,02,\
00,1c,00,01,00,00,00,02,80,14,00,ff,01,0f,00,01,01,00,00,00,00,\
00,01,00,00,00,00,02,00,60,00,04,00,00,00,00,00,14,00,fd,01,02,\
00,01,01,00,00,00,00,00,05,12,00,00,00,00,00,18,00,ff,01,0f,00,\
01,02,00,00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,14,00,8d,\
01,02,00,01,01,00,00,00,00,00,05,0b,00,00,00,00,00,18,00,fd,01,\
02,00,01,02,00,00,00,00,00,05,20,00,00,00,23,02,00,00,01,01,00,\
00,00,00,00,05,12,00,00,00,01,01,00,00,00,00,00,05,12,00,00,00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RsRavMon\Enum]
"0"="Root\\LEGACY_RSRAVMON\\0000"
"Count"=dword:00000001
"NextInstance"=dword:00000001杀掉Trojan.PSW.QQPass类木马后,瑞星监控不能加载的朋友,如果你的系统和瑞星与我的一样——都在C盘,你可将这部分内容(蓝色字体)粘贴到记事本中,保存为Rising.reg(其它文件名也行,但后缀必须是.reg)。然后,双击之,将其导入注册表。试试看。
 附件: 附件:
下载次数:268
文件类型:image/pjpeg
文件大小:
上传时间:2006-8-9 23:13:32
描述:
预览信息: EXIF信息- User Comment : LEAD Technologies Inc. V1.01
 2006-08-30 14:56:22
|